Fraud handling
Fraud handling is a part of Leissner Billing System. Leissner Fraud Detection, analyzes call volume, duration, and utilizes statistics from previous control periods for detecting suspected fraud attempts.
Fraud handling features
- By utilizing a hot-CDR flow directly from the phone switches, the system can instantly tell what’s happening in the network.
- Analyze call behavior in both directions with previous reference periods in order to detect a significant deviation in call behavior.
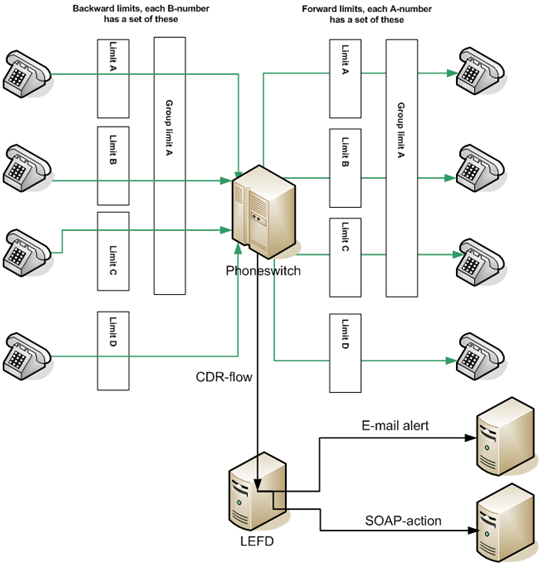
- You can set different limits on different destinations and also group dangerous destinations together in order to detect attacks spread over multiple endpoints.
- The system checks for deviations regarding both the number of calls and call duration.
- Choose how the system behaves once a deviation is detected; the system may both raise the alarm and take automatic action by contacting remote systems via API.
- Endlessly scalable – There is no restriction of how many limits you can configure. You can have one limit for a country, another for a region in the country and a third for a specific endpoint.
Fraud handling
Fraud Detection, a module in Leissner Billing System, analyzes call volume, duration, and utilizes statistics from previous control periods for detecting suspected fraud attempts. Checks are performed per subscriber, destination and/or group of destinations. CDR-files are loaded as they are delivered from the telephony platform(s) and checks are performed within certain time intervals, depending on traffic volume.
The system takes various measures by analyzing data and pinpoints risks based on the parameters specified in the system.
Alarm and block functionality
LEFD doesn’t wait for the attack to complete before it takes action. You can choose how the system behaves once a deviation is detected; the system may both raise the alarm and take automatic action by contacting remote systems via API.
You can have different actions for different deviations, for instance you may want to simply be notified if the number of premium calls increase for a customer, or you can enable the system to directly act by blocking international and costly destinations before the operations team receives the first warning.
Endlessly scalable
Endless scalability, there are no configurable limit restrictions. You can have one limit for a country, another for a region in the country and a third for a specific endpoint. It is up to you to decide what is dangerous and what is trustworthy. Once decided you can put all of the rotten eggs in one basket to even detect attacks spread out over multiple destinations all over the world.
You can also group several customers into a separate group with their own limits; this can be useful as business customers may have more international calls whereas private customers may have more premium calls.


